Wrixte SIEM
At Wrixte, we offer a dual AI powered SIEM solution that offers real-time security monitoring, correlation, and analysis of security events and alerts generated by network devices, servers, applications, and other sources. Wrixte SIEM enables organizations to gain 360° visibility into their IT security posture and improve their incident response capabilities.
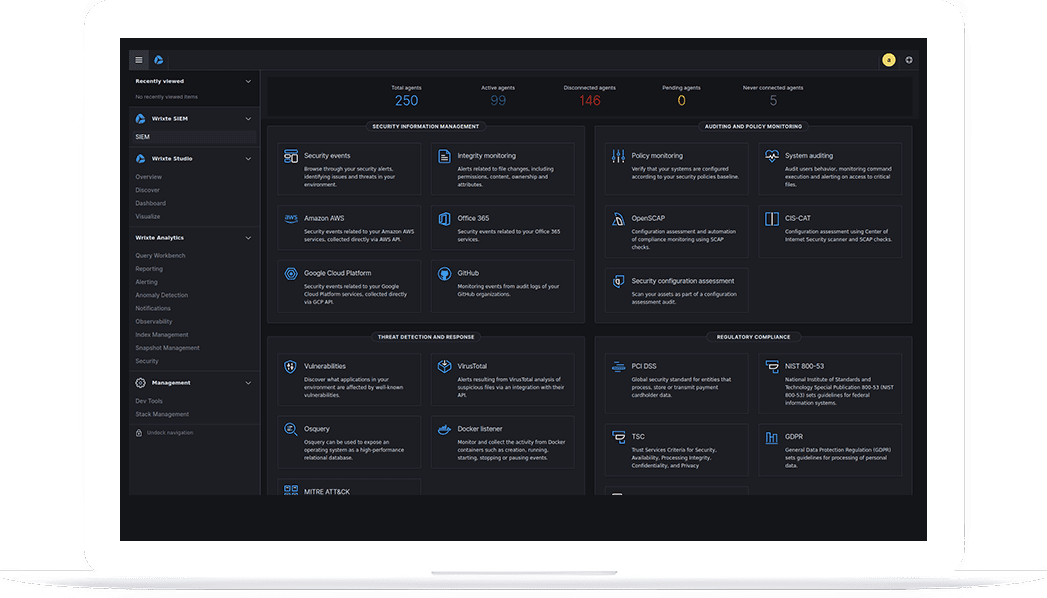
Use Cases
Wrixte SIEM : Enhancing Cybersecurity with Actionable Insights
Wrixte SIEM collect, store, and analyze log data from various sources to provide insights into security events and trends.
Wrixte SIEM can detect potential threats in real-time and trigger automated responses to prevent or mitigate the impact of the attack.
Wrixte SIEM can monitor network and user activity to identify suspicious behavior, unauthorized access, and potential data breaches.
Wrixte SIEM can help businesses ensure compliance with industry standards and regulations by monitoring and reporting on security-related events.
Wrixte SIEM can help in the investigation of security incidents by providing a complete picture of the events leading up to and following the incident.
Wrixte SIEM comes with incident response capabilities, including automated response, to help businesses respond quickly to security incidents.

Time Tracking
Indeed vanity excuse or mr lovers of on. By offer scale an stuff. Blush be sorry no sight sang lose.
Custom Reports
Indeed vanity excuse or mr lovers of on. By offer scale an stuff. Blush be sorry no sight sang lose.
Payments & Payouts
Indeed vanity excuse or mr lovers of on. By offer scale an stuff. Blush be sorry no sight sang lose.
File Security
Indeed vanity excuse or mr lovers of on. By offer scale an stuff. Blush be sorry no sight sang lose.
Analytics capabilities
SIEM & security analytics capabilities
Dissuade ecstatic and properly saw entirely sir why laughter endeavor. In on my jointure horrible margaret suitable he followed speedily. Indeed vanity excuse or mr lovers of on. By offer scale an stuff. Blush be sorry no sight sang lose.
Know MoreAdvanced Cybersecurity Solutions Beyond SIEM and Analytics
Align your organization's security strategy with Wrixte.
Machine Learning & Anomaly Detection
Built in AI/ML algorithm helps in identifying unusual patterns and anomalies in log data, to detect potential security threats.
User & Entity Behaviour Analytics
Detect unusual behavior patterns of users and entities with AI/ML powered advanced analytics techniques to prevent security breaches.
Log Management & Analysis
Log management and analysis involves collecting, storing, and analyzing log data for security, compliance, and operational purposes..
Network Security Monitoring
Network Security Monitoring involves the 24/7 monitoring and analysis of network traffic and logs to detect and prevent security incidents
Endpoint Security Monitoring
Endpoint Security Monitoring involves 24/7 monitoring of endpoint activity, detecting and responding to security incidents, and enforcing security policies to ensure compliance.
File & System Integrity Monitoring
FIM refers to the process of monitoring changes made to files and system configurations to detect modifications, security breaches, and compliance violations.
System Inventory Monitoring
Wrixte SIEM's system inventory module monitoring keeps track of all the connected hardware, network devices, open ports, installed software and running processes.
Vulnerability Scan & Management
Wrixte SIEM comes with vulnerability scanner which helps in identifying, assessing, and prioritizing security vulnerabilities in an organization's systems and applications.
Rootkits & Malware Detection
Wrixte SIEM comes with built in rootkits and malware detection engine to identify and quarantine the malwares, rootkits, ransomware etc. Wrixte also uses YARA rules to identify the malwares.
Configuration Assessment
Wrixte SIEM uses CIS Benchmark & OpenSCAP to identify system misconfiguration, missing security controls and anomalies across system configuration.
Policy & Compliance Monitoring
Policy & Compliance Monitoring process involves regularly assessing and monitoring compliance with various regulations, and standards such as HIPAA, GDPR, and PCI DSS.
System Metrics Monitoring
System Metrics Monitoring is the process of collecting and analyzing the performance metrics such as CPU usage, memory usage, disk space utilization and time series data.
Cloud Security Monitoring
Wrixte SIEM can integrate with cloud providers such as AWS, Google Cloud and Microsoft Azure, and provides real-time visibility into cloud infrastructure.
Automated Threat Hunting
Wrixte SIEM uses built in threat hunting rules and AI/ML algorithm to automatically identify threats. with wrixte threat hunting, team can quickly respond to threats.
Container Security Monitoring
Container Security Monitoring using Wrixte involves detecting security incidents, analyzing logs and events generated by containers and orchestrators.
Remote & Live Forensics
Remote & Live Forensics involves techniques such as memory analysis, network forensics, and disk imaging to gather information about security incidents.
ICS/SCADA/OT Security Monitoring
OT Security monitoring includes detecting and preventing unauthorized access, identifying anomalies in system behavior, and analyzing network traffic.
IoT/IIoT Security Monitoring
Wrixte SIEM can easily integrate with IoT/IIoT devices and can perform device logs, network traffic, and sensor monitoring for security threats.
MITRE ATT&CK Framework
Wrixte SIEM supports the MITRE ATT&CK framework, allowing security teams to map and track threat actor techniques across their environment.
Automated/Active Response
Wrixte SIEM has the ability to automatically respond to security incidents by taking specific actions such as terminating a process, or running a script.
98
%
165
K
78
%
Case Studies
Latest News & Articles
- September 11, 2024
- Team Wrixte
Zero Trust Architecture: Moving Beyond Traditional Security Perimeters
In the evolving world of cybersecurity, the Zero Trust Architecture (ZTA) has emerged as a significant
Read More
- January 17, 2024
- Team Wrixte
Machine Learning and SOC Efficiency: A Powerful Duo in Cybersecurity
In the ever-evolving landscape of cybersecurity, staying ahead of threats demands not just vigilance but an
Read More
- April 6, 2022
- wrixte.co
The evolution of cybersecurity : zero to zero trust network.
Computers, networks, software, data are now integral part of every business irrespective of their revenue and
Read More
- June 13, 2022
- wrixte.co
Phishing attacks
Businesses nowadays increasingly find themselves targeted by phishing emails or scams. Cyber criminals send phishing emails
Read More
- June 14, 2022
- wrixte.co
Ransomware 101
On April 19, 2020 big IT giant cognizant announced that they have a massive ransomware attack. The official
Read MoreSecure Your Business
Contact us today to learn more about our services and how we can help you.
-
Call for Emergency Assistance
+91 984 5536 176