Wrixte Threat Analytics Engine
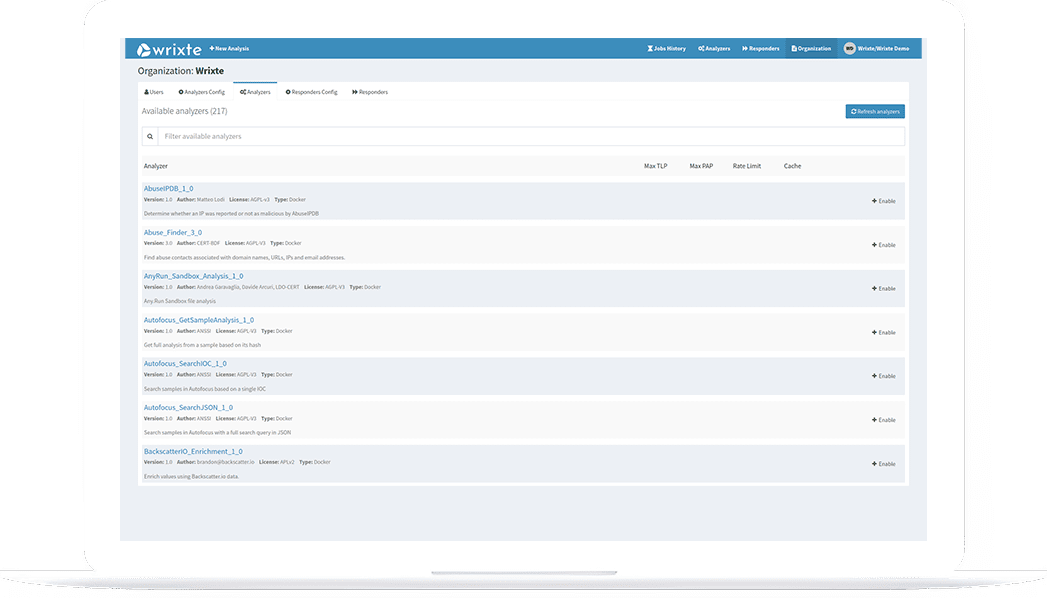
Wrixte Threat Analytics Engine enables security teams to automate threat analysis and incident response processes. It comes with 200+ threat analyzers and 60+ responders which allows the security team to take quick action against the cyber threats. With Wrixte TAE security teams can create custom analyzers, responders, and reports to streamline their incident response workflows.
Features
Automate Cyber Threat Hunting & Incident Response
Analyzer
Wrixte TAE can analyze and extract data from various sources such as URLs, IP addresses, and file hashes. It comes with 200+analyzers which helps teams to save time, reduce errors.
Responders
Wrixte TAE can trigger automated responses based on the analysis results. For example, it can block malicious traffic or quarantine infected machines or block communication etc.
Enrichment
Wrixte Threat Analytics Engine provides automated enrichment of observables with threat intelligence and context data, allowing for more effective analysis and response to security incidents.
Integration
Wrixte TAE can integrate with a variety of tools and platforms such as Wrixte CIM, MISP, SOAR and many more to provide quick threat intelligence, allowing teams to take swift action against threats.
Customization
Wrixte TAE can be customized to fit the specific needs of an organization, security teams can also create custom analyzers, responders, and reports.
Scalability
Wrixte TAE in horizontally scalable and can scale up to handle large amounts of data and analysis requests, making it suitable for enterprise-level security operations.
Collaborative Analysis
Wrixte Threat Analytics Engine enables collaborative analysis of incidents, allowing multiple security team members to work together on a single case and share knowledge.
Metrics and Reporting
Wrixte TAE provides detailed metrics and reporting capabilities, enabling security teams to monitor performance and identify areas for improvement.
Case Studies
Latest News & Articles
- September 11, 2024
- Team Wrixte
Zero Trust Architecture: Moving Beyond Traditional Security Perimeters
In the evolving world of cybersecurity, the Zero Trust Architecture (ZTA) has emerged as a significant
Read More
- January 17, 2024
- Team Wrixte
Machine Learning and SOC Efficiency: A Powerful Duo in Cybersecurity
In the ever-evolving landscape of cybersecurity, staying ahead of threats demands not just vigilance but an
Read More
- April 6, 2022
- wrixte.co
The evolution of cybersecurity : zero to zero trust network.
Computers, networks, software, data are now integral part of every business irrespective of their revenue and
Read More
- June 13, 2022
- wrixte.co
Phishing attacks
Businesses nowadays increasingly find themselves targeted by phishing emails or scams. Cyber criminals send phishing emails
Read More
- June 14, 2022
- wrixte.co
Ransomware 101
On April 19, 2020 big IT giant cognizant announced that they have a massive ransomware attack. The official
Read MoreSecure Your Business
Contact us today to learn more about our services and how we can help you.
-
Call for Emergency Assistance
+91 984 5536 176