- Need Help? Request A Callback
- Working Hours: 9:00 AM – 9:00 PM
Wrixte Cyber Threat Intelligence
Wrixte Cyber Threat Intelligence (CTI) helps in collecting, analyzing, and circulating information about potential or current cyber threats. CTI provides perspective into the tactics, techniques, and procedures used by threat actors, enabling organizations to proactively identify, prevent, and respond to cyber attacks.
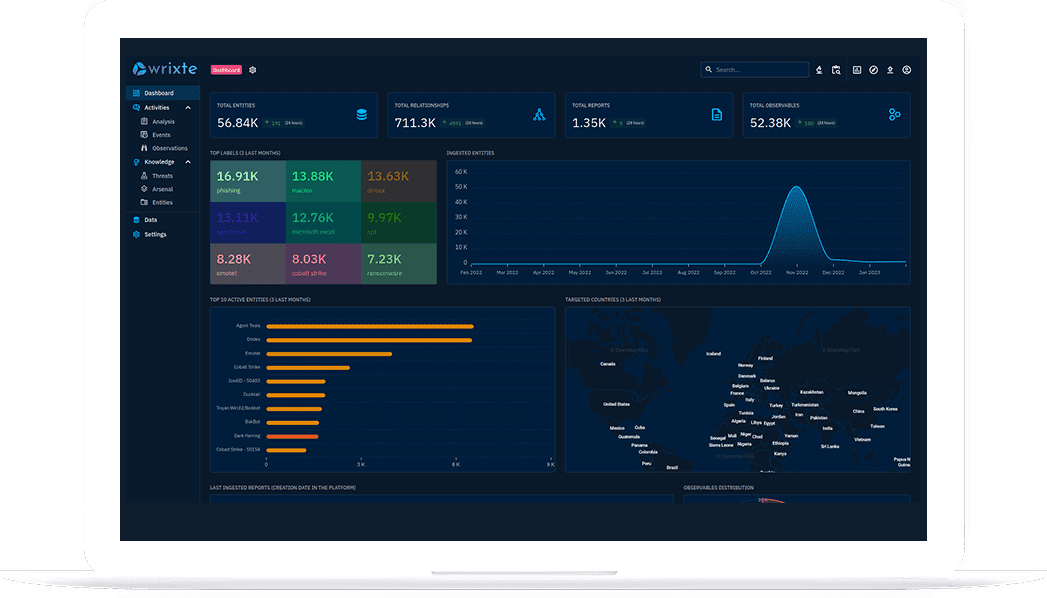
Features
Wrixte Cyber Threat Intelligence : Empowering Your Cybersecurity Strategy
Data Collection
Wrixte CTI can collect and store data from a wide range of sources, including open-source intelligence feeds such as OTX, commercial feeds, and internal security tools.
Data Enrichment
Wrixte CTI can automatically enrich threat intelligence data with additional context, such as indicators of compromise (IOCs), threat actor profiles, and vulnerability information
Visualization
CTI provides a range of visualization tools, including graphs, timelines, and maps, to help understand and analyze complex relationships between threat actors, and incidents
Collaboration
Wrixte CTI supports collaboration between security teams and stakeholders, allowing them to share threat intelligence data, analysis, and insights in a centralized platform
Automation
Wrixte CTI can automate repetitive tasks, such as threat intelligence feed collection and analysis, freeing up security analysts to focus on higher-level tasks.
Scalability
Wrixte CTI is horizontally scalable and supports big data, enabling organizations to manage large volumes of threat intelligence feeds and support multiple users and teams.
Use Cases
Enhancing Cybersecurity Operations: Wrixte CTI Use Cases for Threat Intelligence.
Wrixte CTI can support risk management activities by providing insights into the threats and risks facing an organization, as well as potential impact and likelihood of an attack.
Wrixte CTI can be used to share threat intelligence data between organizations, enabling them to collaborate and collectively defend against cyber threats.
Wrixte CTI can support intelligence analysis activities by providing a centralized platform for collecting, analyzing, and disseminating intelligence data
Wrixte CTI can help security analysts build detailed profiles of threat actors and their tactics, techniques, and procedures (TTPs), providing insights into their motivations and potential targets.
Wrixte CTI can support the development of threat models by providing data and insights into potential attack vectors, allowing organizations to prioritize their cybersecurity investments and activities
Wrixte Cyber Threat Intelligence can inform strategic decision-making by providing data and insights into emerging threats and trends, enabling organizations to develop proactive cybersecurity strategies.
0
M+
0
K+
0
K+
0
+
Case Studies
Latest News & Articles
- September 11, 2024
- Team Wrixte
Zero Trust Architecture: Moving Beyond Traditional Security Perimeters
In the evolving world of cybersecurity, the Zero Trust Architecture (ZTA) has emerged as a significant
Read More
- January 17, 2024
- Team Wrixte
Machine Learning and SOC Efficiency: A Powerful Duo in Cybersecurity
In the ever-evolving landscape of cybersecurity, staying ahead of threats demands not just vigilance but an
Read More
- April 6, 2022
- wrixte.co
The evolution of cybersecurity : zero to zero trust network.
Computers, networks, software, data are now integral part of every business irrespective of their revenue and
Read More
- June 13, 2022
- wrixte.co
Phishing attacks
Businesses nowadays increasingly find themselves targeted by phishing emails or scams. Cyber criminals send phishing emails
Read More
- June 14, 2022
- wrixte.co
Ransomware 101
On April 19, 2020 big IT giant cognizant announced that they have a massive ransomware attack. The official
Read MoreSecure Your Business
Contact us today to learn more about our services and how we can help you.
-
Call for Emergency Assistance
+91 984 5536 176
We use cookies on this website to improve your browsing experience and analyze site traffic. By clicking 'Accept,' you consent to our use of cookies. To learn more about how we use cookies, please read our Privacy Policy.
Accept
Change Settings
Cookie Box Settings
Cookie Box Settings
Privacy settings
Decide which cookies you want to allow.
You can change these settings at any time. However, this can result in some functions no longer being available. For information on deleting the cookies, please consult your browser’s help function.
Learn more about the cookies we use.
With the slider, you can enable or disable different types of cookies:
This website will:
This website won't:
- Essential: Remember your cookie permission setting
- Essential: Allow session cookies
- Essential: Gather information you input into a contact forms, newsletter and other forms across all pages
- Essential: Keep track of what you input in a shopping cart
- Essential: Authenticate that you are logged into your user account
- Essential: Remember language version you selected
- Functionality: Remember social media settings
- Functionality: Remember selected region and country
- Analytics: Keep track of your visited pages and interaction taken
- Analytics: Keep track about your location and region based on your IP number
- Analytics: Keep track of the time spent on each page
- Analytics: Increase the data quality of the statistics functions
- Advertising: Tailor information and advertising to your interests based on e.g. the content you have visited before. (Currently we do not use targeting or targeting cookies.
- Advertising: Gather personally identifiable information such as name and location
- Remember your login details
- Essential: Remember your cookie permission setting
- Essential: Allow session cookies
- Essential: Gather information you input into a contact forms, newsletter and other forms across all pages
- Essential: Keep track of what you input in a shopping cart
- Essential: Authenticate that you are logged into your user account
- Essential: Remember language version you selected
- Functionality: Remember social media settings
- Functionality: Remember selected region and country
- Analytics: Keep track of your visited pages and interaction taken
- Analytics: Keep track about your location and region based on your IP number
- Analytics: Keep track of the time spent on each page
- Analytics: Increase the data quality of the statistics functions
- Advertising: Tailor information and advertising to your interests based on e.g. the content you have visited before. (Currently we do not use targeting or targeting cookies.
- Advertising: Gather personally identifiable information such as name and location
- →
- Contact Us
- Facebook Messenger
- Telegram